E-mail authentication in e-commerce

E-mails are the most frequently used form of communication in e-commerce. In this article, we look at the SPF, DKIM and DMARC frameworks. We show how they can contribute to secure and authenticated emailing.
The importance of emails is often underestimated in e-commerce. Even in smaller stores, the amount of emails sent daily can quickly reach several thousand. In fact, a large part of customer communication in e-commerce happens via e-mail. Frameworks such as SPF, DKIM and DMARC are used to make the sending of e-mails as secure as possible. In essence, all three frameworks aim to make the sender of an e-mail uniquely identifiable to the recipient. All three procedures together provide effective protection against phishing, spam and spoofing.
E-mails in e-commerce
Many e-mails are business-critical and are sent automatically. These include transactional e-mails such as order confirmations, shipping notifications, or sending invoices. The creation of user accounts or the changing of a user password also triggers the automatic sending of an e-mail.
Other use cases include DSGVO-compliant double opt-in or e-mails in the dunning process. Support also often communicates with customers via email in addition to telephone and chat. These types of e-mails are usually necessary to keep a store running productively.
From a marketing perspective, emails are also an important tool in online retail. The most common types of e-mails used in this area include product newsletters, sweepstakes, special offers, new feature announcements, or surveys. In most cases, promotional e-mails are not necessary to ensure the ongoing operation of the store. However, they are an important medium for attracting and retaining customers.
The reasons for communication in e-commerce are manifold and the amount of emails sent can grow quickly. This makes it all the more important to send e-mails in accordance with modern security standards.
Why is secure e-mailing necessary?
Cyber attacks are not limited to websites. Mail servers are also frequently the target of criminal activities such as spam or phishing attacks. Since a lot of sensitive data has to be exchanged, especially in e-commerce, ensuring secure and data-protection-compliant e-mail dispatch is one of the obligations of all store operators.
In e-commerce, store operators primarily act as senders of e-mails. As such, they are interested in ensuring that their domain and sender addresses have a good reputation. This depends, among other things, on how often addresses or domains appear in connection with phishing and spam. It is therefore important for senders to be able to control the use of their own domain and sender addresses as well as possible.
In addition, there is a very practical self-protection, since it should be as difficult as possible, for example, to forge an internal e-mail (for example, from the management to the accounting department) under one's own domain.
With the measures presented below, you can also protect customers of your store. Since most (large) e-mail hosters check the above measures and reject e-mails if necessary, your customers will receive less spam or phishing associated with your domain or sender address. In addition to protecting the customer, this also helps you avoid being associated with these negative experiences in the e-mail inbox.
Measures to secure e-mailing.
In the following, we will show you the means you can use to make your e-mail setup reliable in order to build trusting relationships with your customers.
Use mail-tester.com
Do you already run an online store and send business-critical e-mails in productive operation? With the free, browser-based service mail-tester.com, you can check whether the quality of your e-mail setup is adequate. In addition to a general spam assessment, the use of frameworks such as SPF and DKIM is checked.
In order to use mail-tester.com, you first have to clarify what kind of e-mail delivery you want to check. For example, if you want to check the quality of your order confirmations, an order confirmation must also be sent to the service. If, for example, the newsletter dispatch is to be checked, on the other hand, a newsletter issue must be sent. Sending a generic test e-mail, for example with Outlook or Thunderbird, will not provide a robust result for other, specific e-mails.
At mail-tester.com, an individual e-mail address is generated for you, to which you send the e-mail to be tested. Deposit this e-mail address, for example, with a test user account in your store and then use it to place an order. The "Then check your score" button displays the analysis result of the last e-mail received at this address.
The score that mail-tester.com gives out is based on the content of the message, the sender addresses and other parameters. The score has a value from one to ten, with ten being the best possible value.
In addition to the score, the details are presented in a report. This also provides information about settings and services that may not yet have been configured correctly. The report therefore provides excellent indications of the areas of e-mail dispatch where there is still room for improvement.
You can also forward the link to a report to service providers such as us for advice or to have necessary adjustments made directly by the relevant experts. In the free version of the tool, the analysis results of a specific e-mail are available for a total of seven days.
Use SPF
Using SPF (Sender Policy Framework) reduces the risk of spam for your customers. It makes it more difficult for unauthorized third parties to use protocol sender addresses from your domain. The SPF procedure determines which servers are allowed to send an e-mail with a protocol sender address assigned to a specific domain.
If configured accordingly, SPF contributes to a better reputation and improves the deliverability of own e-mails.
The SPF procedure is based on the fact that a domain owner specifies for a domain which servers in the Internet are allowed to send e-mails with protocol sender addresses of this domain. The list of these authorized servers is stored in the DNS, the Domain Name System.
For this purpose, a so-called SPF record is entered in it. This record of the type TXT ultimately contains the IP addresses of all servers that are allowed to send e-mails assigned to the domain.
However, many recipients are not familiar with the IP addresses. In addition, they are also used by authorized service providers and can also change. For these reasons, the SPF record allows aliases and references to other domains. For example, if you use a service provider to send newsletters or host your mailboxes, they will usually provide you with an extension for your domain's SPF record that references the service provider.
Using the domain's SPF record, the receiving mail server can check whether an email sent to it comes from an authorized mail server. If this is not the case, the e-mail is classified as 'untrusted' and usually declared as spam. The only requirement for this is that SPF is supported by the recipient system. This is the case with just about every e-mail provider.
SPF only affects the protocol sender address used when sending between two e-mail servers. This is normally invisible to the recipients of an e-mail when they view it. SPF is therefore not related to the normal sender address that is displayed to recipients in the e-mail program.
SPF entries must be checked and, if necessary, adjusted for all changes related to e-mails. Indeed, once such an entry exists, it is usually binding and exclusive. It follows that servers not named in the SPF entry are also not allowed to send e-mails. For example, if you forget to adjust it after switching to another newsletter provider, the emails from the new provider will hardly reach their recipients. There are some typical changes that need to be taken into account: These are, for example, new or discontinued third-party providers of ticket systems, newsletter or billing service providers, or even the complete change of the email hoster.
Deploy DKIM
The DKIM (DomainKeys Identified Mail) identification protocol can be used to ensure the authenticity of e-mails. The use of this method serves as verification and ensures that an e-mail has not been modified by the sending mail server since it was sent. This prevents subsequent changes to the e-mails, for example to the sender's address, the subject or the content.
Especially with the signature of the sender address, which is directly displayed to the recipient of the message, it can be made clear to a certain extent that an e-mail is trustworthy because it really comes from the contained sender domain. Whether and how the specific signature information is checked and displayed to the recipient depends on the e-mail hoster and/or the e-mail program.
What does DKIM do?
With the help of DKIM, store operators can add a "digital signature" to their e-mails. Each outgoing e-mail and much of the information it contains is cryptographically signed by the sending mail server in the so-called DomainKey-Signature header.
The receiving mail server can use the public key contained in the DNS to verify that an e-mail has not been modified after it has been sent. In addition, it is possible to compare the signature key used with the domain of the sender named in the e-mail. This procedure can help to curb phishing. It also makes it more difficult to manipulate business-critical information in e-mails.
How does DKIM work?
The DKIM process is based on asymmetric cryptography. To create a digital signature, selected information is combined into an e-mail and passed through a cryptographic function together with the secret (private) key. The result, i.e. the signature, is stored in coded form in the e-mail headers.
The receiving mail server can verify the generated signature using the public key. The cryptographic process ensures that this check fails if the message has been modified or the wrong key has been used. In addition, it can be indicated whether a signature also originates from the domain of the sender's address. This ensures that the e-mail is authentic. If this is not the case, the received e-mail can be rejected or classified as 'not trustworthy', respectively changed afterwards.
To use DKIM for your domain, a two-step setup is required. The first step involves setting up the signatures themselves. Without this step, outgoing emails will not be signed. If you work with service providers who send emails on your behalf, they sometimes already take care of this step automatically. Otherwise, it is often sufficient to activate DKIM in the settings of your domain at this service provider. Under certain conditions, maxcluster also offers to set up DKIM for you.
The second step is optional and involves the creation of a similar DNS record as already done for SPF. Such a DNS record must exist, but not necessarily be created at the domain used for the sender address. If a service provider uses its own domain as the signature domain, no additional entry is required at the domain of the e-mail sender address.
Whether the DNS entry is required and what it looks like in concrete terms thus depends on the type of setup at the respective service provider. Entries of the type TXT or CNAME are possible. If you host your e-mails yourself, a TXT entry is usually used.
The DKIM DNS entry legitimizes the use of the signature key used for your domain by publishing the public key and meta information about it there. Similar to SPF, it makes sense to check and update the DKIM entries stored in the DNS when changes are made to the e-mail dispatch.
It can happen in rare cases that e-mails are subsequently modified for legitimate reasons and thus fail a DKIM check. For example, mailing list subject lines can be changed. It can also happen that, for example, a virus scanner adds a header line that was not there before and should actually be part of the signature. However, these cases have become increasingly rare since the spread of DKIM and can usually be rectified in the short term.
Deploy DMARC
DMARC (Domain-based Message Authentication, Reporting and Conformance) is used to specify a policy for sending e-mails from a domain. This policy builds on SPF and DKIM. The DMARC procedure allows domain owners to tell receiving mail servers whether and under what criteria e-mails from their domain should be checked for SPF compliance and DKIM signatures. In addition, recommendations for action can be specified on how to deal with e-mails that do not pass these checks.
What does DMARC do?
DMARC is the logical complement to SPF and DKIM to achieve (almost) complete authorization of e-mails, i.e. verification of the authenticity of sender and content. In this way, DMARC helps to curb phishing, spam and spoofing.
For the sender domain, it specifies how the receiving mail system should perform authentication. In addition, if authentication by SPF and/or DKIM fails, recommended actions can be transmitted to the recipients.
In addition, you can use DMARC to check whether there are authentication problems when sending your e-mails. Using the report fields within DMARC, reports can be requested from receiving mail servers. From this, conclusions can be drawn about misconfigurations or the use of your own domain by spam or phishing, if necessary.
How does DMARC work?
DMARC acts as a control and guideline for the use of SPF and DKIM. Consequently, the procedure can be most usefully employed when SPF and/or DKIM have been previously established.
DMARC makes it possible to establish a link (alignment) between the sender address and the domains of the protocol sender address (SPF check) on the one hand and the DKIM signature domain (DKIM check) on the other.
DMARC is set up via the DMARC entry, which is stored in the DNS of the sender domain. This is created on the subdomain _dmarc in the form of a TXT record. For example, if the domain is "maxcluster.de", the corresponding DMARC record can be found under _dmarc.maxcluster.de.
DMARC and SPF: With respect to SPF, DMARC checks whether the sender address of the sent e-mail displayed to the recipient matches the domain of the protocol sender address (checked by SPF).
DMARC and DKIM: With respect to DKIM, DMARC checks the origin of the cryptographic signature. The procedure matches the domain of the signature key with the domain of the displayed sender address.
For both checks, it is possible to specify whether subdomains are also allowed or whether the domains must match exactly.
DMARC policies can specify three different recommended actions for failed SPF or DKIM checks. These define how the receiving mail server should handle messages that fail the authentication process.
- none: If set to none, mail should be delivered to the recipient even if the checks and/or the sender address link are not passed.
- quarantine: E-mails that fail authentication shall be automatically moved to the recipients spam folder with the quarantine setting.
- reject: With the reject setting, all emails not authenticated with DMARC should be automatically rejected. In most cases, senders will receive an undeliverable message from the receiving mail server.
However, for consistent verification of authenticity, it is necessary that all mail servers use the DMARC procedure when receiving an e-mail. This is now already the case with many well-known e-mail providers.
In addition, it is possible to be informed about the failure of SPF, DKIM or DMARC examinations. For this purpose, an e-mail address is published within the DMARC entry, to which corresponding reports can be sent. These reports have a high frequency when a domain is used widely, as is common in e-commerce. They are formatted in XML for automatic evaluation and therefore offer little overview without appropriate evaluation software. For this reason, reports are primarily suitable for immediate monitoring after changes have been made to authorization procedures.
Use captchas
A widely used method to protect against misuse of one's own e-mail addresses and servers is the use of captchas. These assist in distinguishing bots from real users. Captchas can be used to make it more difficult to access certain page elements that generate automated e-mails.
What do captchas do?
Captchas perform a gatekeeper function, making it difficult to access interactive page elements such as login forms or areas. The method poses an obstacle to the automatic filling of forms by bots, since in addition the included captcha must be "solved".
A captcha can take a variety of forms. There are text-, image- or audio-based captchas that require, for example, the recognition of a term or a sequence of numbers. The respective solution must be entered in the corresponding input field. Simple checkboxes that have to be clicked manually are also possible.
In e-commerce, captchas keep spam bots from exploiting forms and login screens to automatically generate emails on behalf of site operators. Captchas can also be an aggravator for real users from a user experience perspective.
How do captchas work?
In order to include a captcha on a website, various third-party services can be used. Probably the best known service is Google's reCAPTCHA. There are also application-specific third-party plugins for Shopware, Magento or WordPress. These can be purchased and implemented via the respective store or marketplace.
A captcha integrates with your web pages, so to use it you can usually enlist the support of your agency or developers. Using a captcha is always useful in addition to the methods already mentioned, because a captcha prevents legitimate applications, services or servers from being exploited for malicious purposes.
For the best possible protection of your domain(s), use SPF, DKIM, DMARC as well as captchas and also maintain these measures permanently.
E-mail hosting at maxcluster
All hosting packages at maxcluster include Managed E-Mail and Managed DNS by default. In the e-mail area, we rely on the common standards for spam prevention. We allow easy setup of mailboxes and forwarding via our Application Center. Our redundant DNS servers can also be easily managed via this.
Initial setup of SPF, DKIM and DMARC by our service team is not included in our services by default. While setting up SPF or DKIM records on our DNS servers is straightforward, DKIM signatures and signature checks and DMARC are not supported on the central mail servers. If you have any questions about this, our service team will be happy to help you. Please call +49 5251 414130 or send an e-mail to support@maxcluster.de. In our Knowledge Base you will also find further information and recommendations on the configuration of SPF, DKIM and DMARC.
Conclusion
E-mail is one of the most important elements of e-commerce. Authentication methods such as SPF, DKIM and DMARC increase security and trust in the senders of business-critical e-mails. Captchas ensure that legitimate email sources are not abused by spammers. The risk of spam, phishing and spoofing is effectively reduced by combining the above procedures. Consistent use of these frameworks protects domain operators and their customers.
SPF, DKIM, DMARC and captchas ensure that legitimate e-mails do not end up in the spam folder and that abusive e-mails are rejected by recipients. In this way, store operators ensure that business-critical e-mails such as order confirmations or invoices are reliably received by buyers.
Published on 23.06.2023 | DR, SL
You have questions, requests, criticism, suggestions or just want to tell us your opinion about our blog? Here you have the opportunity to contact us directly.
Send e-mail
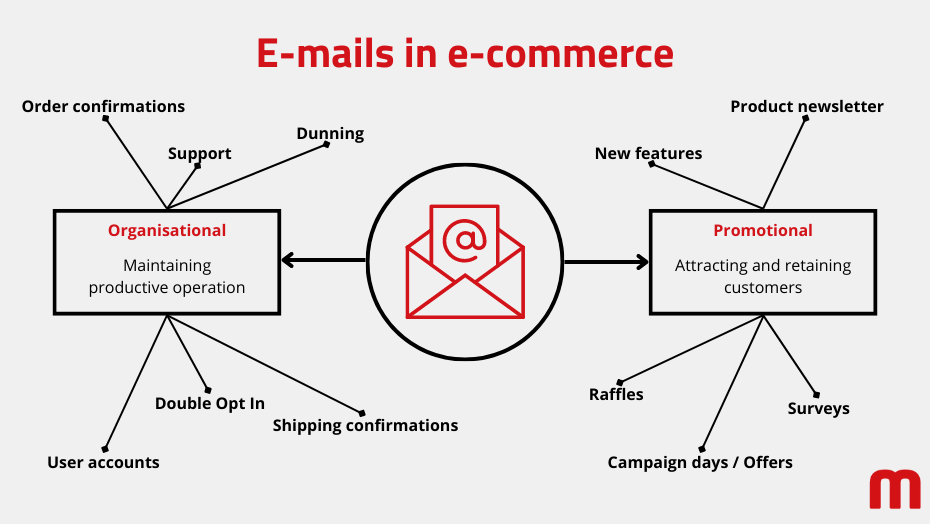 E-mail types in e-commerce | Illustration: maxcluster
E-mail types in e-commerce | Illustration: maxcluster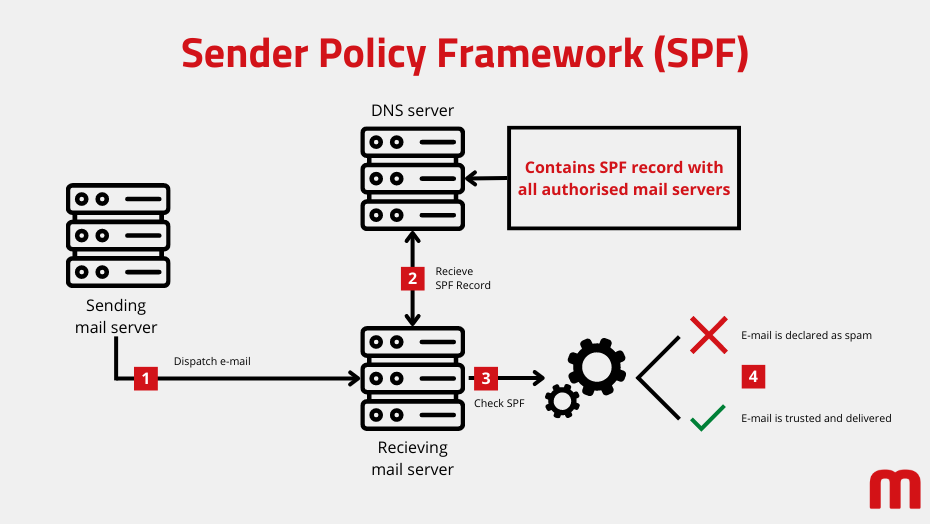 How SPF works | Illustration: maxcluster
How SPF works | Illustration: maxcluster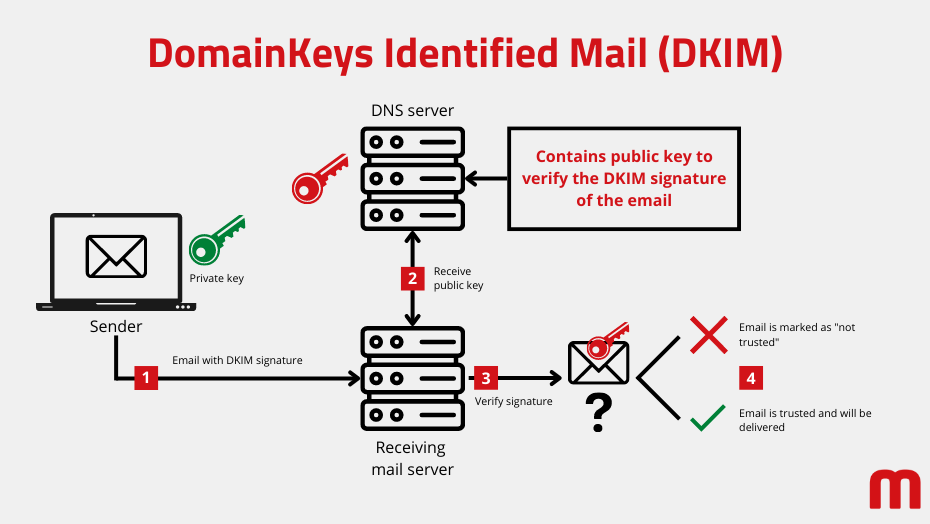 How DKIM works | Illustration: maxcluster
How DKIM works | Illustration: maxcluster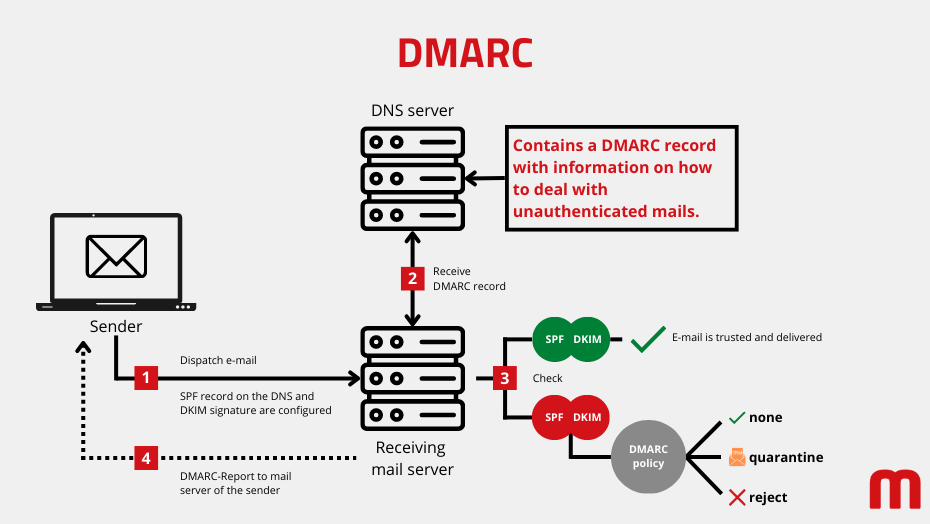 How DMARC works | Illustration: maxcluster
How DMARC works | Illustration: maxcluster