Knowledge
Know-how for the operation of online shops
Knowledge is also the key to success in e-commerce! As a hosting provider, we want to support online shop operators, developers and agencies with our expertise and experience in their daily work in the best possible way.
On this platform, we share useful knowledge in the form of white papers, e-books, blog posts and configuration guides to make both small and more complex online shops even more performant, stable and secure.
Discover categories:
- Show all categories
- Knowledge
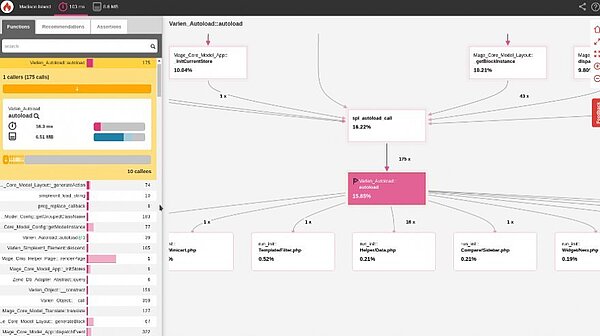
Knowledge Base
Unsere erweiterte Knowledge Base flaniert ab jetzt unter knowledge.maxcluster.de. Aber keine Sorge, unsere Suchfunktion hilft ihnen weiterhin den richtigen Artikel zu finden.
Whitepaper
E-Books
Neuste Blogbeiträge
Seite 1 von ?