Old TLS versions
Security issues in TLS due to outdated versions
Details:
TLS is the successor standard to SSL and is used for the encrypted transmission of web pages. The TLS standard, which is continuously being developed, must meet high security requirements because it is used for very many important online activities, including online banking and of course online shopping/e-commerce. TLS connections are established between the browser and the web server, and the web server and browser must support at least one common version. However, supporting old TLS versions to cater to potential customers with old devices often comes at the expense of security for all site users. For example, with TLS version 1.0, there are several known security vulnerabilities (e.g., BEAST, CRIME) that allow a third party to read the contents of encrypted connections. With TLS 1.1, the encrypted connection cannot rely on modern encryption and integrity techniques such as AES and SHA2, which could facilitate attacks. Due to compatibility with existing implementations, these security vulnerabilities cannot always be fixed without a version update.
With the stipulation of the Payment Card Industry (PCI), which became effective on 06/30/2018, online stores with PCI DSS certification can no longer use TLS 1.0.
Solution: Disable TLS 1.0 and 1.1.
Disable TLS versions 1.0 and 1.1 via the Managed Center of your cluster. The function is located under the menu item of the web server active on your cluster.
By clicking the green button "TLS Version" you will be shown the available TLS versions and you can disable TLS 1.0 or TLS 1.0 & 1.1.
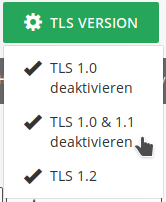
The deactivation applies to all domains set up on your cluster and can be reversed at any time. Since the web server will be restarted when a change is made, there will be a short interruption in availability.
More informations
- The timing for the changeover is very controversial for TLS versions. The US-CERT (Computer Emergency Readiness Team) in the USA has recommended to deactivate TLS 1.0 (and older versions) on 04/30/2015. The Federal Office for Information Security in Germany (BSI) recommended as early as 2014 in its guideline TR-02102-2 to no longer use TLS 1.0 and extended this recommendation to TLS 1.1 at the beginning of 2016. Since the end of 2019, the SSL test by Qualys has been awarding a maximum grade of "B" (instead of the maximum grade of "A+") for domains that still offer TLS 1.0 or 1.1.
- The current TLS version 1.3 was released on August 10, 2018. It has been supported by the major browsers Firefox and Chrome since October 2018, as well as by Safari (> 12.1) on macOS (from version 10.14.4), and by Microsoft since January 2020 with the migration of its Edge browser to the Chromium substructure Source: (caniuse.com).
- All four browsers mentioned will no longer support the old TLS versions 1.0 and 1.1 with the versions coming out in March 2020. This is to protect users from establishing encrypted connections with potentially vulnerable encryption methods to old servers. A majority of web users will then only use TLS 1.2 and TLS 1.3.
- On the server side TLS 1.3 spreads slower, because here the update cycles are considerably longer and several components must play together. Under Linux, OpenSSL version 1.1.1 or higher is required first. In addition, the appropriate version of the web server is needed - for Apache this is the case with 2.4.37 and for NGINX with 1.13.0. The specification of TLS 1.3 appeared after the last Ubuntu version with long-term support (18.04 LTS), so we will offer you the latest version at a later time.

