
In the upcoming posts, we'll explore together how you can secure various aspects of your online shop to enhance your customers' trust and keep hackers at bay. Are you ready to expand your knowledge and make your shop more secure than ever before?
Cyber Attacks on Online Shops: The Recent Alarm Bells
In recent years, the threat of cyber attacks on online shops has dramatically increased. Companies of all sizes have become targets for hackers looking to steal sensitive customer data and inflict significant financial damages. Online security is one of the most crucial topics that you not only should but must address. Not every company can afford a specialist in this field, yet there are numerous ways to ensure the security of your online shop and adequately protect it from cyber attacks.
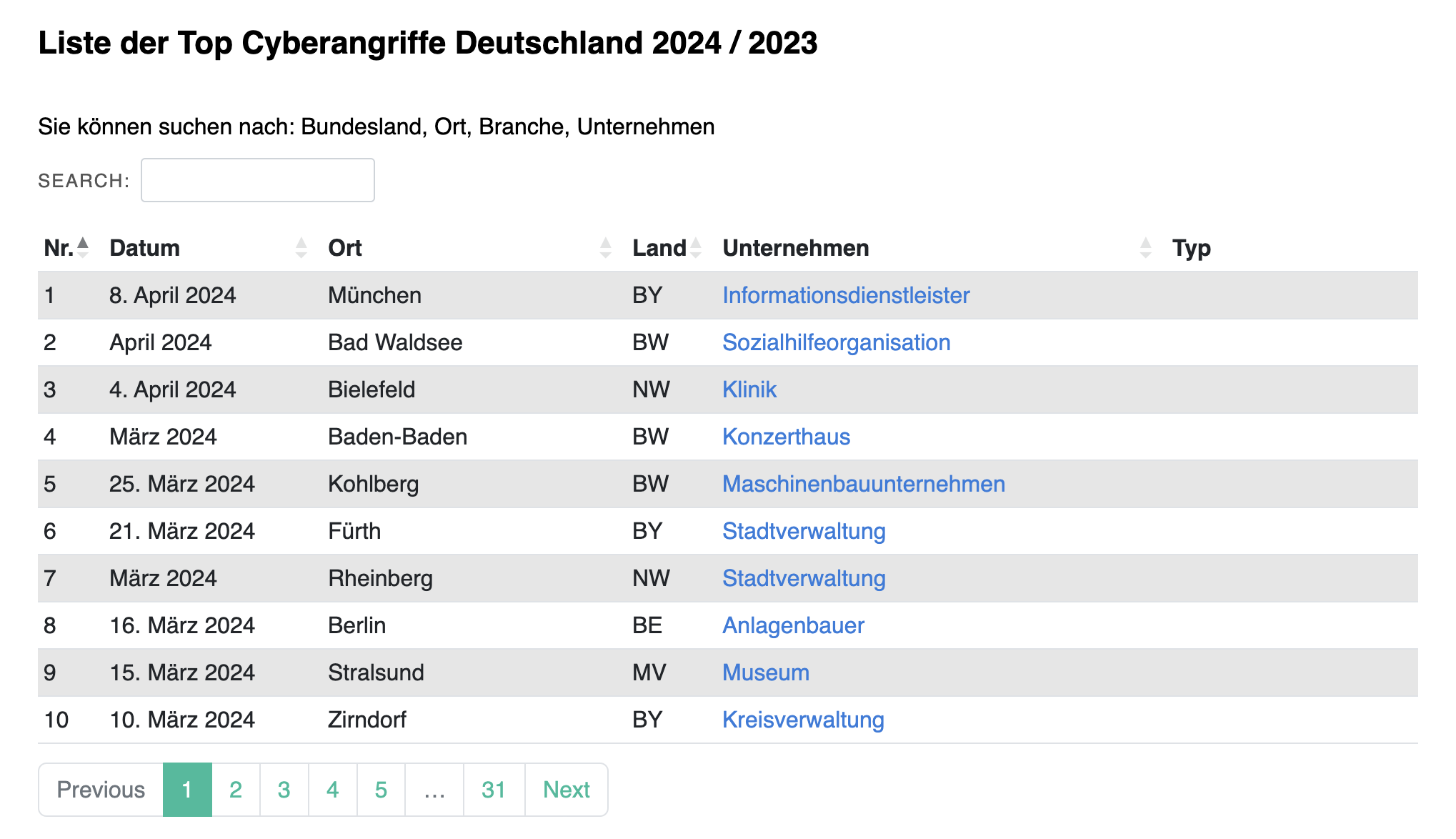
Looking at current statistics can be quite unsettling. Hacker attacks occur almost weekly worldwide, and even large companies are not always shielded from such assaults. A notable example of a hacker attack on online shops is the incident involving Thalia in 2022. Thalia, a popular online bookstore, fell victim to a cyber attack where hackers utilized a brute-force attack to gain access to thousands of customer accounts.
Brute-Force Attack
During a brute-force attack, an attacker attempts to gain access to a system or account by systematically trying all possible password combinations until the correct one is found. The attacker typically employs automated programs or scripts to try a large number of passwords in a short time. This type of attack is particularly effective against weak passwords, as the attacker can simply try all possible combinations until finding the right one. The complexity and length of a password usually determine how long it takes to crack it through a brute-force attack. Brute-force attacks can be conducted in various ways, such as on websites, email accounts, and encrypted data. It is a widespread and dangerous method through which hackers gain access to sensitive information.
Magecart Attacks
Another significant phenomenon is the so-called Magecart attacks. Magecart is a hacker group specializing in injecting malicious code into payment forms of online shops. Through such attacks, data from millions of customers have already been stolen, leading to significant financial losses for the affected companies. The security of your online shop is not only a matter of protecting sensitive customer data but also a crucial factor in earning your customers' trust and thus the success of your business. A successful hacker attack can not only result in financial losses but also profoundly shake customers' trust and damage your reputation.
Furthermore, many countries are legally obliged to comply with data protection regulations and securely store personal data. Violating these regulations can lead to significant fines and jeopardize the survival of your company.
How Secure Is My Online Shop?
There are various ways to improve the security of your online shop. Some measures you can take on your own, while others should be handled by your hosting provider. By the way, it's always advisable to discuss security enhancement options with your current hosting provider and ensure you're always up to date.
Your Checklist for Online Shop Security:
SSL Certificate: Ensure that your online shop uses a valid SSL certificate to establish a secure and encrypted connection between the customer's browser and your server. An SSL certificate (Secure Sockets Layer) is a digital certificate that encrypts and authenticates a website's security. Its purpose is to establish a secure connection between the user's browser and the server hosting the website. Essentially, an SSL certificate works by encrypting sensitive data transmitted between the user's browser and the server. This means that even if a hacker intercepts the traffic, the information cannot be readily read or understood. An SSL certificate is primarily used for e-commerce websites, online banking, social networks, and other websites where transmitting sensitive information like personal data, credit card information, or passwords is necessary. Moreover, an SSL certificate indicates to website visitors that the site is legitimate and their data is being transmitted securely. You can obtain an SSL certificate from various Certificate Authorities offered by most web hosting providers. Some web hosting providers also offer free SSL certificates, while others provide paid options with advanced features and security levels. It's crucial to ensure that the SSL certificate is issued by a trusted Certificate Authority to ensure the security and authenticity of your website.
Regular Updates: Keep your e-commerce platform and all used plugins or extensions up to date to patch known security vulnerabilities. Regularly visit the official website of your e-commerce platform (e.g., Shopware, Magento, Wordpress…) to look for new plugins or extensions. Many platforms have a marketplace or library where developers publish their extensions. Subscribe to newsletters or notifications on your e-commerce platform's website. Often, platforms send regular updates and announcements about new plugins or extensions via email.
Strong Passwords: Use strong, unique passwords for all administrator accounts and access to your shop, and enable two-factor authentication where possible. A strong password should meet several criteria to ensure your online shop's security:
- Length: A strong password should be at least 12 characters long. The longer the password, the more difficult it is for an attacker to crack it. Complexity: A strong password should include a mix of uppercase letters, lowercase letters, numbers, and special characters. Use a variety of characters to make the password more complex. Uniqueness: Never use the same password for multiple accounts or websites. Instead, use a unique password for each administrator account and access to your shop.
- Avoid dictionary words: Do not use easily guessable words or phrases, as they are susceptible to dictionary attacks. Instead, you can use a passphrase consisting of a random combination of words to enhance security. An example of a strong password could be: "Tr0tz!Gehe1mSe1n@". This password meets all the criteria mentioned above as it is long, includes a mix of uppercase letters, lowercase letters, numbers, and special characters, is unique, and does not use easily guessable dictionary words.
- In addition to using a strong password, it is advisable to activate two-factor authentication where possible. Two-factor authentication adds an extra layer of security by requiring an additional confirmation step, such as a one-time password sent to your mobile phone.
Firewall and Security Software: Install a firewall and reliable security software to protect your shop from malicious attacks. For the e-commerce sector, various firewall and security software solutions are available to help protect your online shop from malicious attacks. Here are some popular options:
- Web Application Firewall (WAF): A Web Application Firewall is specifically designed to protect web applications from attacks such as SQL injections, Cross-Site Scripting (XSS), and other web-based threats. Popular WAF solutions for the e-commerce sector include Cloudflare, Sucuri, and ModSecurity.
- Antivirus and Antimalware Software: Reliable antivirus and antimalware software is essential to protect your online shop from malware infections and other harmful attacks. Known antivirus and antimalware solutions for the e-commerce sector include Norton Security, McAfee, Kaspersky, and Bitdefender. Intrusion Detection
- System (IDS) / Intrusion Prevention System (IPS): An Intrusion Detection System (IDS) or Intrusion Prevention System (IPS) monitors the traffic on your network and detects potentially malicious activities or attacks. Popular IDS/IPS solutions for the e-commerce sector include Snort, Suricata, and Cisco Firepower.
- Security Software Suites: Many providers offer comprehensive security software suites that combine various security features such as firewall, antivirus, antimalware, IDS/IPS, and more. Examples of such security software suites include Norton 360, McAfee Total Protection, and Kaspersky Internet Security.
Payment Processing Verification: Ensure that the payment processing in your shop complies with applicable security standards and is regularly monitored. The applicable security standards for payment processing in your online shop are typically set by the Payment Card Industry Data Security Standard (PCI DSS). This standard was developed to protect sensitive credit card data and ensure that it is processed and stored properly. To ensure that your payment processing complies with the applicable security standards, you can take the following steps:
- Consult the official PCI DSS website: The official website of the PCI Security Standards Council provides comprehensive information about PCI DSS and the requirements for secure payment processing. Here you will find detailed information about each requirement and the corresponding controls.
- Contact your payment provider: Your payment provider should be able to provide you with information about which security standards apply to the payment methods they support. They can also help you verify whether your payment processing complies with the applicable standards and whether any adjustments are necessary.
- Hire a security service provider: You can also hire an external security service provider to conduct a comprehensive security assessment of your payment processing and provide recommendations for improvement. These providers are often specialized in compliance with security standards such as PCI DSS and can provide valuable insights.
Penetration Testing and Audits: Conduct regular penetration tests and security audits to identify and address potential vulnerabilities in your shop. Penetration tests and security audits are essential tools for identifying security flaws and weaknesses in an online shop or other IT infrastructure. Here's an explanation of what they are and why they are important:
- Penetration Tests (also known as Ethical Hacking or Pen-Tests): Penetration tests are controlled attacks on a computer system or application conducted by an authorized security expert. The goal of a penetration test is to assess the security measures of a system by applying various attack techniques that a potential attacker could use. This helps uncover vulnerabilities and security flaws that could allow an attacker to infiltrate the system or compromise sensitive data.
- Security Audits: Security audits are systematic evaluations of a company's security policies, procedures, and controls. They are conducted to ensure that a company's security measures are appropriately implemented and effective. Security audits can be conducted internally or externally and often include a comprehensive review of security policies, access controls, network configurations, software patches, and more.
How maxcluster Keeps Over 1500 Online Shops Secure
Patches & Updates are the cornerstones of IT security. In our daily interactions with over 1500 customer online shops, we recognize the immense importance of online shop security. For us, it is essential to stay up to date with the latest technology and continuously engage with this crucial topic. We place great importance on ensuring that our customers feel extremely secure with us. Therefore, one of our unique selling points is making security a priority.
Our approach to online shop security encompasses various aspects, including software lifecycle management, regular patches and updates, and the implementation of backup solutions for web applications.
Another crucial aspect to which we pay special attention is compliance with the General Data Protection Regulation (GDPR) in e-commerce. We work closely with our customers to ensure that their online shops comply with applicable data protection regulations and safeguard their customers' privacy.
In our upcoming blog posts, we will delve into detail on how we at maxcluster ensure that our customers' online shops are optimally protected. We will provide insights into our security practices and demonstrate how we leverage the latest technologies and best practices to ensure our customers' security. So, stay tuned to learn more and take your online shop to the next level of security!
