What is Voxility and what are DDoS attacks?
Voxility is a company that specialises in protecting against DDoS attacks. These "distributed denial of service" (DDoS) attacks are used by cyber criminals to render applications, web services or the firewall incapacitated through a targeted attack on the server. This is done by overloading the infrastructure.
For a DDoS attack, the attackers first infect one or more computers with malicious code. From the resulting infected computer network, the so-called botnet, cybercriminals then remotely attack a specific target. In the process, the target is inundated with countless requests and the infrastructure is thus rendered inoperable. The more computers there are in this botnet, the more powerful the attack.
Servers without DDoS protection are overloaded by this attack and can no longer perform their web services, or only to a limited extent. In this way, the application can no longer be reached by end customers.
There are two main attack scenarios: Attacks at the network level (layers 3 and 4) and at the application level (layer 7). In the following, we explain these two scenarios in more detail.
Layer 3 and 4 – Attacks on the network layer
Network layer attacks, also known as Layer 3 and 4 attacks, are used to clog connections in the network. This form of DDoS attacks is the most common. They are usually reflection attacks such as User Datagram Packet (UDP) floods, synchronised floods or Network Time Protocol (NTP) amplification attacks. By flooding with data packets or requests, the target system is ultimately overloaded.
Often, 20 to 40 gigabits per second of data traffic is enough to render most network infrastructures inoperable. In 2017, an average attack size of 112.8 Gbit/s was measured in DDoS attacks. Voxility offers network protection with a volume of 1,000 gigabits per second. With this DDoS protection, we protect our entire network. This automatically protects our customers from layer 3 and 4 attacks at no additional cost.
Among other things, we secure our customers against the following attack scenarios at the network level:
Attacks on the application layer – layer 7 attacks
Attacks on layer 7 are directed against the application layer. These attacks occur significantly less than Layer 3 and 4 attacks, but are much more complex. The attacks on the application layer concentrate on the layer 7 features, such as HTTP, SNMP or FTP.
The most common method is HTTP flood. If several requests are sent simultaneously to a server, the server needs some time to answer the last request. This limitation can be exploited by a cybercriminal in an HTTP flood. He sends out as many requests as possible, for example for newsletter registration, which overload the server or cause it to crash. In doing so, the hacker could programme through a simple script that he will not accept any responses from the server. Or he could programme that a new request is made to all sub-pages in response to the server's reply. With both methods, the server is overloaded. This type of attack is difficult to identify.
The size of application layer attacks can usually be measured in requests per second (RPS), with no more than 50 to 100 RPS needed to cripple most medium-sized websites.
Effective Layer 7 DDoS protection is very complex. This protection must be set up, configured and maintained individually. For each domain, for example, the SSL certificate must be made available and an SSL proxy must be configured. Our focus was on central DDoS protection, which is why we only offer protection for Layer 3 and 4.
If you are interested in Layer 7 protection, we recommend Cloudflare. If you need assistance, please contact our support team via email at support@maxcluster.de.
How Voxility works during a DDoS attack
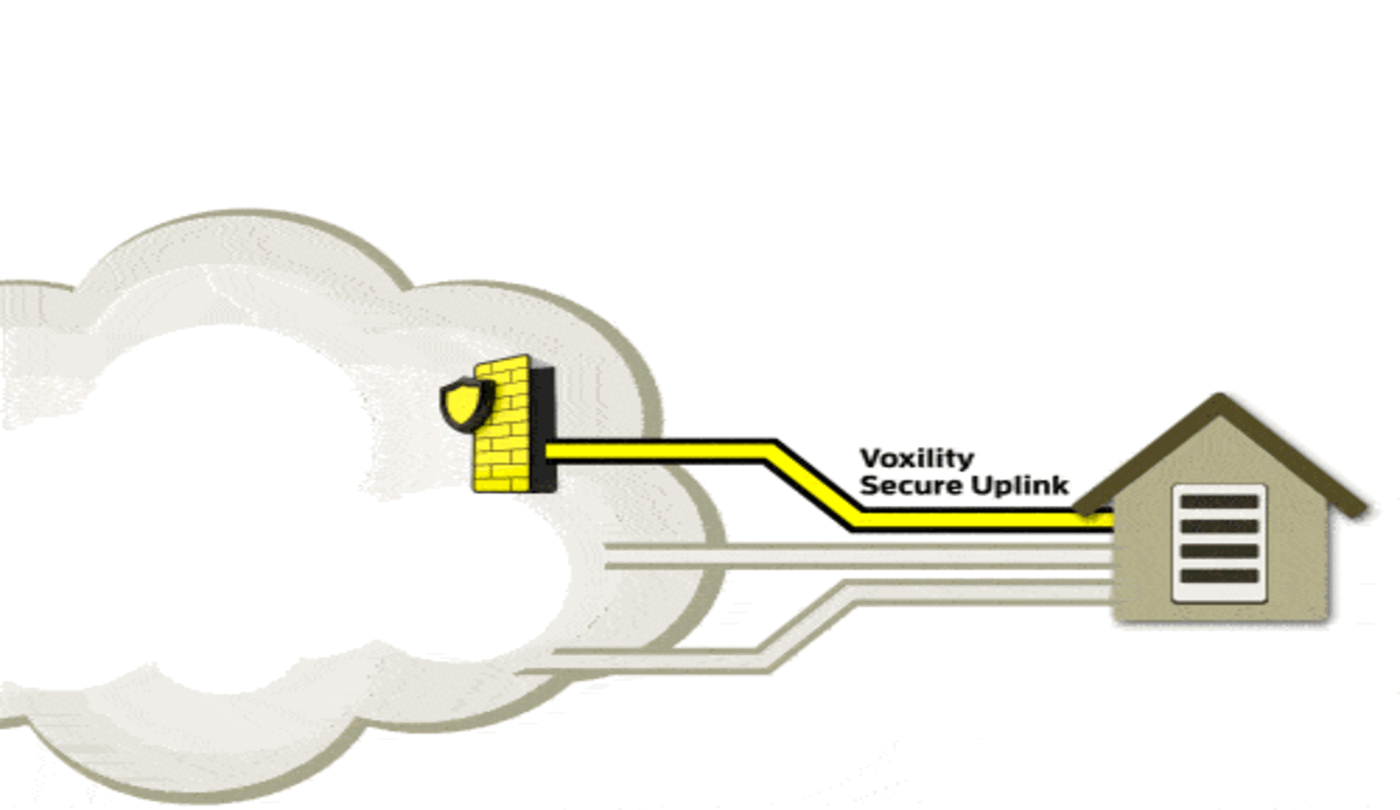
Source: Voxility.com, 2018
A visitor accesses an IP from a data centre. Then a cybercriminal floods the data centre with DDoS traffic, causing the uplinks to become heavily congested. The attacked networks are immediately relieved by a secure uplink and the data traffic is redirected via this secure link to Voxility's network. There, it is examined for various attack scenarios at the network level.
So before the data stream even arrives at our German data centre in Frankfurt, it has already been checked by Voxility. This protects our servers and the entire network from layer 3 and 4 attacks.
Voxility has implemented sensors that permanently monitor the network. Attacks can be identified immediately and the data stream is redirected to a security cloud. The redirection stops a few seconds after the attack has ended. This does not lead to an increase in page loading time or latency.
During an attack, the server remains accessible through Voxility and the web services can be used normally. All non-relevant ports are blocked during the attack, such as ICMP for ping queries. In total, the network is protected up to an attack strength of 1,000 gigabits per second. DDoS attacks are usually on a much smaller scale. The strongest measured attack so far was directed against GitHub with 1,350 gigabits per second, but even there the attack could be intercepted by DDoS protection.
Why do we use Voxility?
We have set ourselves the goal of protecting all our customers from DDoS attacks at the network level, and we do this at no extra cost to the customer.
When looking for a suitable provider, it was important for us to implement a network solution that filters the data traffic even before it arrives at our data centre in Frankfurt. This way, the entire network is protected.
We have already rolled out DDoS protection in a multi-stage system within the last three months.
What are the advantages of protection through Voxility?
Voxility offers the following advantages compared to other DDoS protection solutions:
Through our use of Voxility, the risk of a DDoS attack is minimised in advance. With effective anti-DDos protection in place, the prospect of a successful attack by cybercriminals is very low. In addition, the likelihood of cybercriminals launching an attack at all has been reduced to a minimum.
Are there any disadvantages?
In a shop with a lot of traffic, there may be a delay of 3 to 5 milliseconds in the initial setup between server and client. This is because Voxility analyses the data packets of the already high traffic for the attack scenarios.
Conclusion
We are convinced that Voxility's central DDoS protection effectively protects our customers against network attacks on Layer 3 and Layer 4. Compared to other providers, Voxility protects against attacks up to 1,000 Gbit/s. This does not result in any additional costs for our customers.
If you have any questions, please contact our maxcluster support team at 05251/41 41 30 or via e-mail supportmaxcluster.de.
